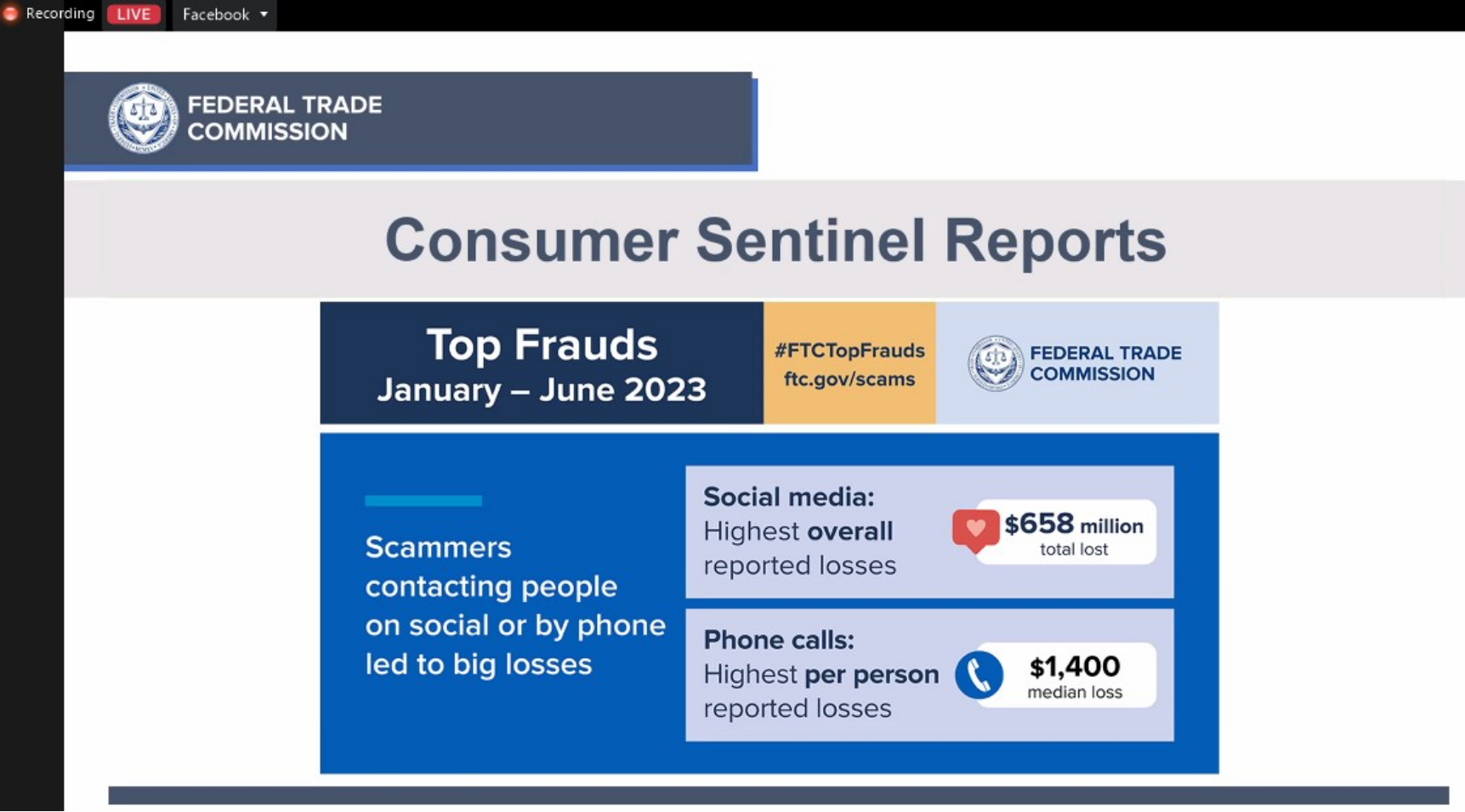
According to a report by the U.S. Chamber of Commerce, the Federal Trade Commission (FTC) received over 1.1 million complaints of business fraud from January to June 2023, with losses totaling $4.4 billion. Business fraud is on the rise across the United States, with no signs of slowing down.
In a webinar on September 22, 2023, FTC Market Director Greisman said that overpayment fraud has become one of the most common payment scams. She explained that someone will send you a check that is more than the amount you owe, and then ask you to wire the difference back to them. The problem is that the original check is often fake, and by the time you realize it, you have already sent your own money to the scammer.
Overpayment Fraud: Types
Overpayment fraud is a type of fraud in which a scammer tricks a seller into sending them money by pretending to have overpaid for a purchase. The scammer will often use stolen credit card information to make a purchase, then ask for a refund for the excess amount. The scammer will then request that the excess be returned to another payment account or third-party source, in order to convert available credit balance or credit limit into cash.

Fake Check
Fake check scams involve a scammer sending a fake check to an individual or business, enticing them to deposit the check and then send back part of the money or pay for certain services. These scams are often targeted at e-commerce merchants and individuals who are seeking work-at-home opportunities or conducting business with people they do not know.
The following are the steps involved in a fake check scam:
The scammer sends the seller a fake check, the amount of which is usually more than the agreed-upon price for the goods or services being sold. The scammer tells the seller that they accidentally overpaid, and requests that the excess amount be returned. The seller ships the goods, and then returns the excess amount to the scammer; the bank discovers that the scammer's check is fake. The seller loses the goods. Fake check scams can cause significant financial losses to individuals and businesses. It is always advisable to verify the authenticity of checks and payment methods before taking any action, and to be cautious when dealing with individuals who request refunds or overpayments without a legitimate reason.
Fake Customer Overpayment
Fake customer overpayment is a type of fraud in which a scammer uses stolen credit card information to make a purchase from a merchant that accepts stolen credit cards. They intentionally overpay for the product or service, and then request a refund for the excess amount, usually through a different payment method or by requesting a cash refund.
The following are the steps involved in the scam:
The scammer uses a stolen credit card to make a purchase from a merchant, intentionally overpaying the product or service fee. The scammer then contacts the buyer, claiming that they made a mistake, and requests that they refund the excess amount. The scammer provides the seller with another payment account, such as bank account details or other credit cards. The seller, unaware of the fraudulent nature of the initial payment, processes the refund, effectively transferring legitimate funds to the scammer. The cardholder discovers that their credit card has been stolen, and contacts the issuing bank to request a refund to recover the lost funds. The seller not only loses the goods and the sale price, but also the funds they "overpaid" for the refund, as well as any resulting chargeback fees.
Anti-Fraud: How to Prevent "Overpayment" Fraud
Now that we understand what overpayment fraud is, the next consideration is how to effectively prevent it. Dingxiang Anti-Fraud Cloud Business Intelligence Center experts recommend taking a multi-pronged approach, including transaction security, transaction identification, technical identification, and team security knowledge training.
Strengthen Transaction Security
Increase the security of payments, reduce the risk of malicious transactions, and create a more secure and reliable payment environment.
Adhere to payment transaction security standards. Ensure that all devices have their default passwords changed and that cardholder data is encrypted. At the same time, establish an effective firewall between the internet and the system used to store data, and create a unique identity identification code for users who process credit card data. Use the Credit Card Verification Value (CVV). The CVV is a three-digit or four-digit security code printed on the credit card. The payment processing system will automatically verify these numbers and confirm or reject the user's transaction request based on their validity, to ensure the user's legitimacy. Use the 3DS verification service. The 3DS verification service is a network security authentication service launched by international card organizations such as Visa, MasterCard, and JCB. Before making an online purchase with a credit card, the user needs to enter a pre-set password to confirm that the cardholder is actually making the online transaction.
Strengthen Abnormal Transaction Identification
The following measures can effectively identify potentially risky abnormal orders and take necessary verification measures to protect the rights and interests of merchants and consumers.
Pay attention to the consistency of billing address and shipping address. If the billing address and shipping address are different, this may be a risk signal for an abnormal order. In this case, we can ask the buyer to provide credit card statements, corresponding cardholder driver's license photocopies, phone numbers, etc., or to conduct a phone verification to confirm the buyer's identity. Be wary of the same person placing multiple orders with different cards. If you find that the same person places multiple orders with different credit cards, this may also be a risk signal for an abnormal order. You can ask the buyer to provide additional identity verification or conduct a phone verification to verify the buyer's identity information. Pay attention to the sudden increase in the number of orders. If the order quantity suddenly increases significantly, this may also be a risk signal for an abnormal order. In this case, we can ask the buyer to provide additional identity verification or conduct a phone verification to ensure the buyer's real identity. Pay attention to the sudden change in the amount of consumption. If you find that the consumption amount is small and suddenly becomes huge, this may be a risk signal for an abnormal order. We can ask the buyer to provide further identity verification, such as credit card statements, driver's license photocopies of the cardholder, and conduct a phone verification to verify the buyer's identity. Pay attention to buyers who urge delivery. If the buyer repeatedly urges the merchant to ship the goods after the purchase, this may also be a risk signal for an abnormal order. In this case, you can ask the buyer to provide additional identity verification or conduct a phone verification to ensure the buyer's real identity. Pay attention to buyers with different credit cards and shipping addresses. If the buyer uses a domestic card, but the shipping address is in another country, this may be a risk signal for an abnormal order. We can ask the buyer to provide additional identity verification or conduct a phone verification to verify the buyer's identity information. Pay attention to the behavior of multiple cards trading under the same IP address. If you find multiple different credit cards trading under the same IP address, this may also be a risk signal for an abnormal order. We can ask the buyer to provide additional identity verification or conduct a phone verification to ensure the buyer's real identity.
Using Anti-Fraud Technology Identification
Dingxiang Anti-Fraud Cloud Business Security Intelligence Center recommends that, in terms of fraud prevention, it is necessary to have accurate identification, effective defense, and continuous evolution.
Accurate Identification
tion
By using external mobile number risk scores, IP risk libraries, and proxy email detection tools, you can timely identify malicious mobile numbers, IP addresses, and email addresses, and by detecting the legality of the device fingerprint and the existence of injection, hook, and simulator risks, you can timely identify malicious devices.
Effective Defense
Combined with Dingxiang Anti-Fraud Cloud and Dingxiang Dinsight, build a risk management system that combines machine learning and rule-driven approaches. Through multi-dimensional and in-depth analysis, it can accurately identify abnormal operations and users, and take necessary measures to prevent fraud.
Continuous Evolution
Based on business data and risk data, establish a local name list dynamic operation and maintenance mechanism, consolidate and maintain the corresponding black and white list data, and timely update the risk strategy. At the same time, use the xintell intelligent model platform to build proprietary risk models, explore potential risks, and improve the security level of social media.
Strengthening Team Fraud Training
Regularly hold fraud knowledge training for team members, explaining the different types of overpayment fraud and the abnormal events that need to be paid attention to, and providing skills for handling suspicious transactions and escalating issues when necessary. Through fraud training, the aim is to raise the awareness of fraud among team members, enhance their ability to identify and prevent fraud, and thus reduce the occurrence of fraud.
Here are some specific examples of how anti-fraud technology can be used to identify and prevent overpayment fraud:
Machine learning can be used to identify patterns of behavior that are indicative of overpayment fraud. For example, a machine learning model could be trained to identify users who frequently place orders with different credit cards, or who make orders for large amounts of goods that are shipped to different addresses. Rule-based systems can be used to identify transactions that meet certain criteria that are indicative of overpayment fraud. For example, a rule-based system could be configured to flag transactions that are for more than a certain amount, or that are made by users who have recently opened new accounts. Device fingerprinting can be used to identify malicious devices that are being used to commit overpayment fraud. For example, a device fingerprint could be used to identify devices that are running malicious software, or that are connected to a network that is known to be associated with fraud. By combining these different technologies, businesses can create a more comprehensive and effective anti-fraud strategy that can help to protect them from overpayment fraud.