As one of the basic components of the business system, device fingerprinting is widely used in scenarios such as marking, tracking, temporary credentials, analysis, and anti-fraud, and is an important part of the security system.
Device fingerprinting collects information of the device, and then gives the device a unique identification, and uses association and similarity search algorithms to ensure the stability of the identification.
The information data collected and reported by the device can be used to analyze the common location of a device associated account, the active time period of the device, and whether the device is risky.
The device portrait is constructed from multiple dimensions, and the risk of the current device is presented to the user in real time. That is to say, through device fingerprinting, it is possible to learn the behavior habits, network environment, device portrait, location information, and behavior information of the account, which is helpful in identity verification, security protection, and marketing. At the same time, collecting information and data precipitation through device fingerprinting provides strong support for data analysis, risk control decision-making, and model construction.

Device identification is at the core of device fingerprinting, and it only works if it can accurately identify the devices in the network. Device fingerprinting information involves features including operating system, system plug-ins, browser language settings and time zone, hardware ID, mobile phone IMEI, network card Mac address, font settings, LBS address, etc. Consider AISecurius device fingerprinting, the collected information mainly includes three parts: hardware, network, and system.
Hardware properties: Device brand, model, IMEI (International Mobile Equipment Identity), processor, memory, resolution, brightness, battery, gyroscope, Bluetooth MAC, wireless MAC, factory logo.
System properties: System, version, language, Ls location, boot time, running time, battery status, whether the device is abnormal, whether it is rooted/jailbroken, whether device information has been tampered with, and whether there are cheating tools.
Network properties: WiFi network, carrier network, signal strength, base station information.

Based on the collected information, AISecurius device fingerprinting is capable of monitoring the running status of the device, detecting root (illegal file reading, anti-security detection), automated tools (batch registration, activity cheating), simulator (automatic account registration, automatic order), multi-account (false cheating), keep account active), change device, group control (bogus transaction, fake traffic), app repackaging (plant advertisements, crack restrictions), assisting the risk control and anti-fraud system to identify false registrations, account hacking, malicious logins, bogus transaction, promotion cheating, and keep account active in scenarios such as registration, login, marketing, transaction, top-up, and promotion, and take preventive measures.
Identify machine attack Machine attack/script attack is generally carried out through automated scripts or tools by initiating requests to the target website in batches and automatically. Risk identification of device fingerprinting is capable of identifying whether the request is initiated by machine or script.
The device fingerprint technology can be used to identify account registrations on the emulator, a large number of registrations on the same device within a certain period of time, and whether the registered device is high-risk.
Similarly, in the login scenario, it can effectively identify the risk of frequent login attempts and credential stuffing on the same device, and identify whether the login device is frequently switched.
In a marketing campaign, general campaign rules will limit the same device with the same account to one entry. Device fingerprinting technology can quickly identify whether multiple accounts are bound to the device, and whether the same account is logged in on multiple devices.
Identify channel cheating: In scenarios such as application promotion and display advertising, speculator may use technical tools to obtain promotion fee by forging traffic data. Fake machines and fake installations of real machines are identifiable through device fingerprint technology, so as to effectively track channel traffic and performance.
Identify simulator/debugging risk: Device fingerprinting is able to detect device terminal environment and runtime risks, such as emulator, jailbreak, debugging, injection, framework attack, etc.

In big data analysis and machine learning scenarios, AISecurius device fingerprinting can be used as basic field to observe business indicator data from another perspective and perform correlation analysis. For example, analyze the number of active devices, the number of new devices, the models used by users, the number and amount of transactions on the same device, and the number of users accessing the same device. When building an association, in addition to using the user's mobile phone number and card number, the device ID can also be used as node to observe the relationship between users.
Based on AISecurius device fingerprinting information and business data mining, using application graph data mining, unsupervised algorithm, semi-supervised algorithm, and supervised algorithm to fully mine, combined with application scenarios and the specific needs of actual operators, it is intuitively and intelligently presented on the operation and monitoring platform the most valid information, in order to provide anti-fraud and precision marketing services for multiple industries and scenarios.
Build an associative graph: Based on device fingerprinting information and business data, and understanding of scenario requirements and business logic, build a cross-department and cross-product complex network covering individual, device, organization, product, and transaction.
Association relation mining : Based on device fingerprinting information and business data, extract static portraits of individuals and groups, analyze dynamic trends, locate potential fraud through graph data mining technology, conduct in-depth mining, feature derivation, and apply machine learning quantitative analysis to develop an anti-fraud model.
Self-upgrading: Based on device fingerprinting and business big data, precipitate risk data, accumulate defense strategies, build exclusive risk control models, and implement changes to device fingerprints to upgrade device fingerprint security and prevention and control.

AISecurius device fingerprinting supports Android, iOS, H5, which is capable of detecting simulator, system reinstallation, root jailbreaking, and injection attack, with fast response, efficient risk identification, more than 99% stability and 100% uniqueness.
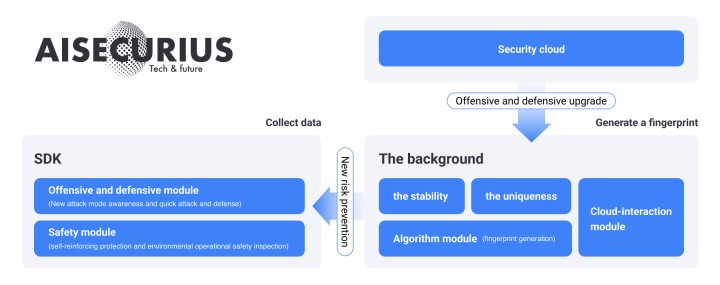
Three unique features of AISecurius device fingerprinting:
First: fast responsiveness. The defensive system must react to the illegal and semi-illegal behaviors is hidden behind the Internet business, which requires device fingerprinting technology to quickly perceive risks and quickly upgrade prevention and control in the face of new attack methods. It has to be able to capitalize on the offensive and defensive experience and risk data precipitation of industries, through the cloud + terminal method, to carry out rapid protection upgrade, and solve the business risks within one attack and guard cycle.
Second: efficient risk identification capability. Device fingerprinting requires security detection capabilities for the basic environment and runtime of the device, and capable of accurately identifying different risks, such as emulator, root, jailbreak, debugging, code injection, multi-account, and VPN proxy. For example, iOS platform hook, jailbreak behavior, Android root, debug, memory dump, injection, multi-account, simulator, vulnerability attack, browser color depth, resolution on the web, the compatibility and consistency of the browser with the system and UA, whether cookies are disabled, etc.
Third: 99% or higher stability and 100% uniqueness. The SDK code of the device fingerprint itself needs to be protected to prevent the collection logic from being cracked and data being forged, and guarantee authenticity and accuracy of source data. Regardless of tampering with device parameters (including IMEI, MAC address, AndroidId, SIM card information, model, and brand), or disabling or clearing cache and cookies, the device fingerprinting must remain unchanged with at least 99% of stability. The fingerprints of any two devices cannot be the same. The device fingerprint ID generated for each device needs to be 100% unique and cannot be tampered with.


