Android App Defender
1. Product Introduction
AISecurius Android application defense is defense-in-depth security system, provides security protection from code security, resource file security, data security and runtime environment security. At the same time, each dimension is divided into different levels, and the defense strategy can be customized according to the actual scenario to achieve the perfect balance between security and performance.
2. Product features
At present, Android defense mainly includes dex files overall protection, Java code virtualization protection, so file protection, html/js protection, game-related script protection, local data protection, and runtime protection.
2.1 dex file overall protection
Carry out dex file overall protection by encrypting the original DEX file, and using anti-JAVA code decompilation and JAVA character constant encryption.
Overall protection of the dex file will hide the original dex file code, making it impossible to find the original dex content with reverse tool:

Anti-java decompilation prevents the decompilation tool from directly decompiling the code into java, improving the difficulty of reverse analysis, including but not limited to (JEB, jd-gui, jadx):
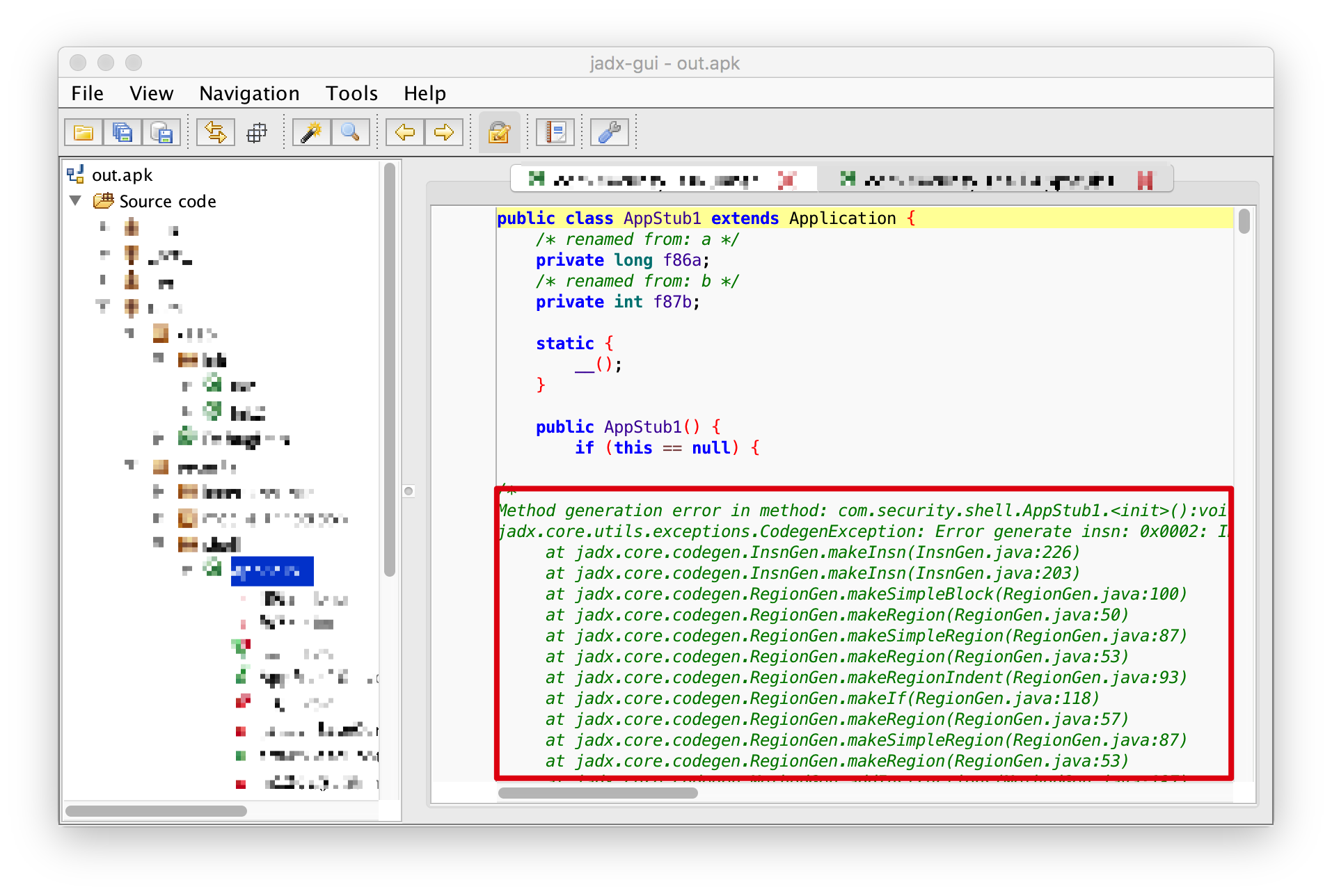
JAVA constant string encryption will hide the plaintext constant strings in the code, increasing the difficulty of reverse engineering
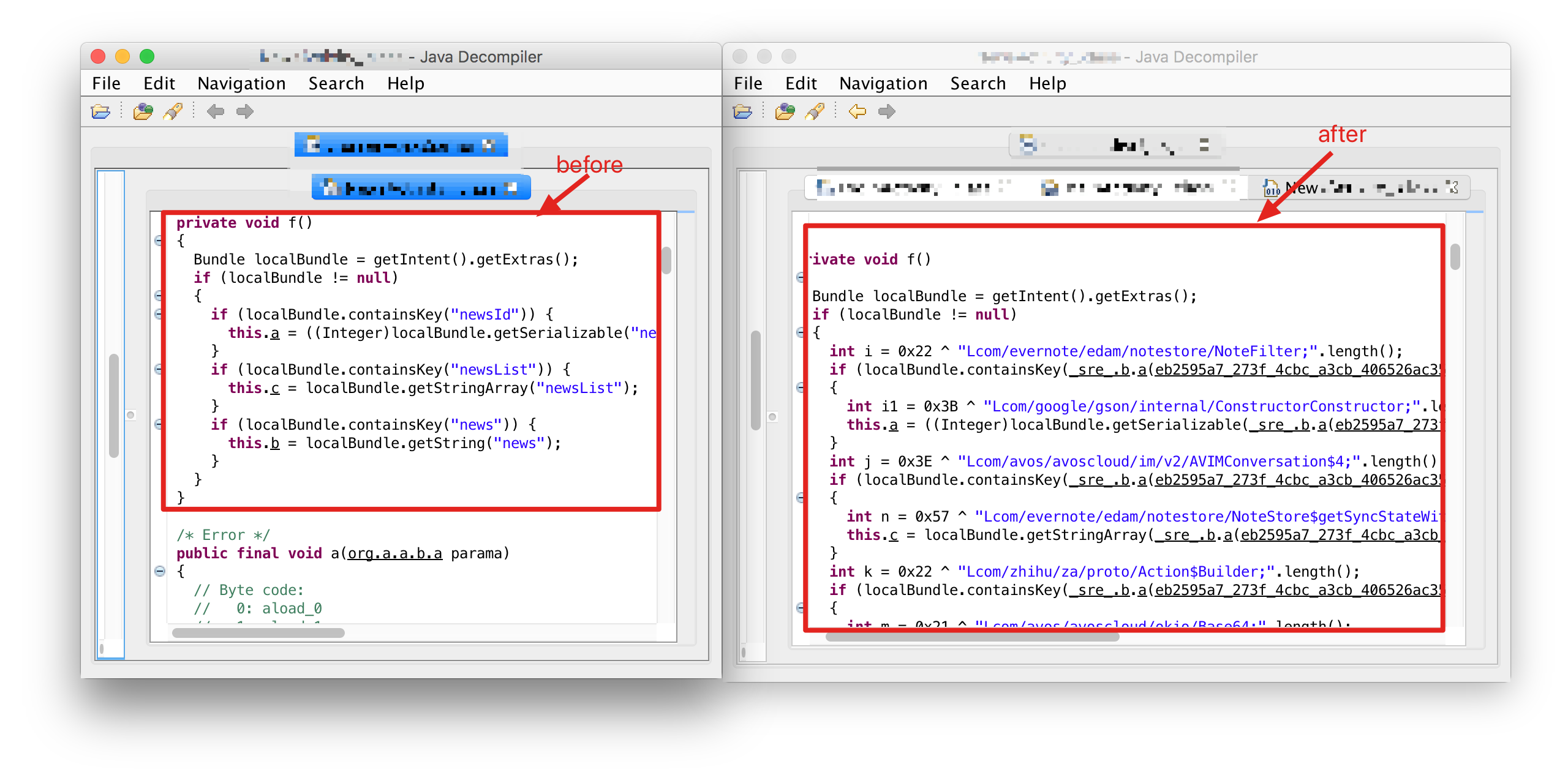
2.2 java code virtualization protection
Compile the original java code into DX-VM virtual machine instructions, and run on the DX virtual machine, which cannot be decompiled back to readable source code. No tool is able to decompile virtual machine instructions.
After java code virtualization, the decompiled the source code will not show anything that may give away original code, and the function body only contains calls to the virtual machine subsystem
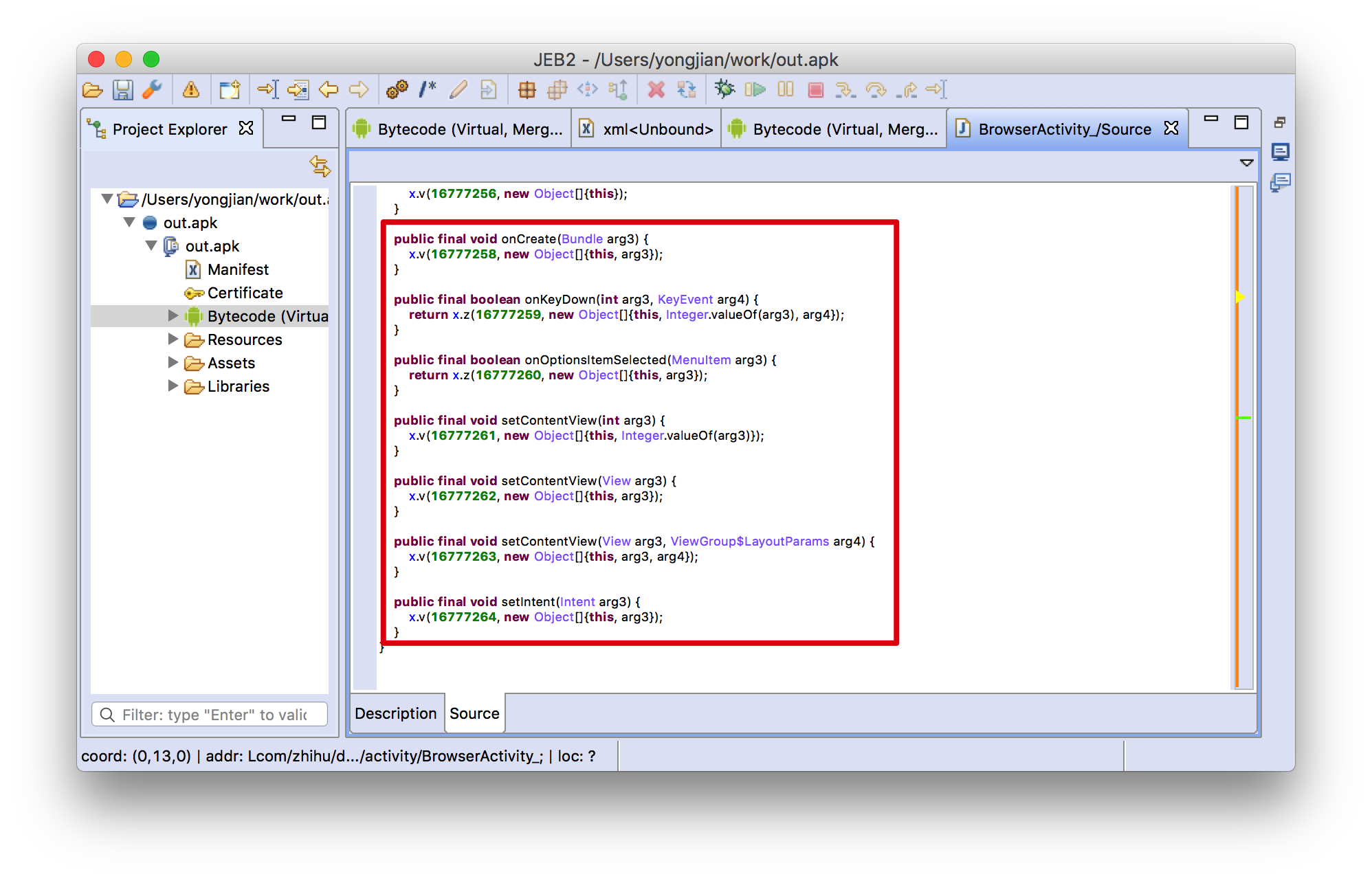
2.3 SO file protection
All-round protection of SO files by decompiling, tamper-proof, anti-theft, virtual machine protection, and code compression for SO files.
Mainstream decompilers are unable to analyze the protected so file
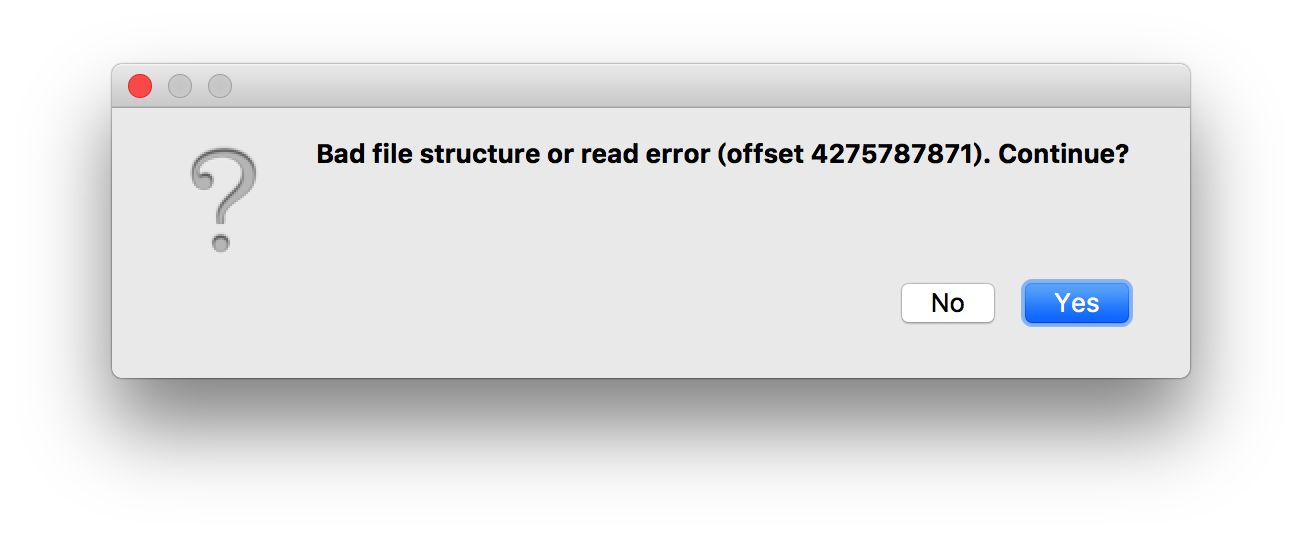
2.4 html/js protection
All-round protection of html/js by tamper-proofing and encryption of html/js files.
html/js protection makes it impossible to get plaintext html/js file
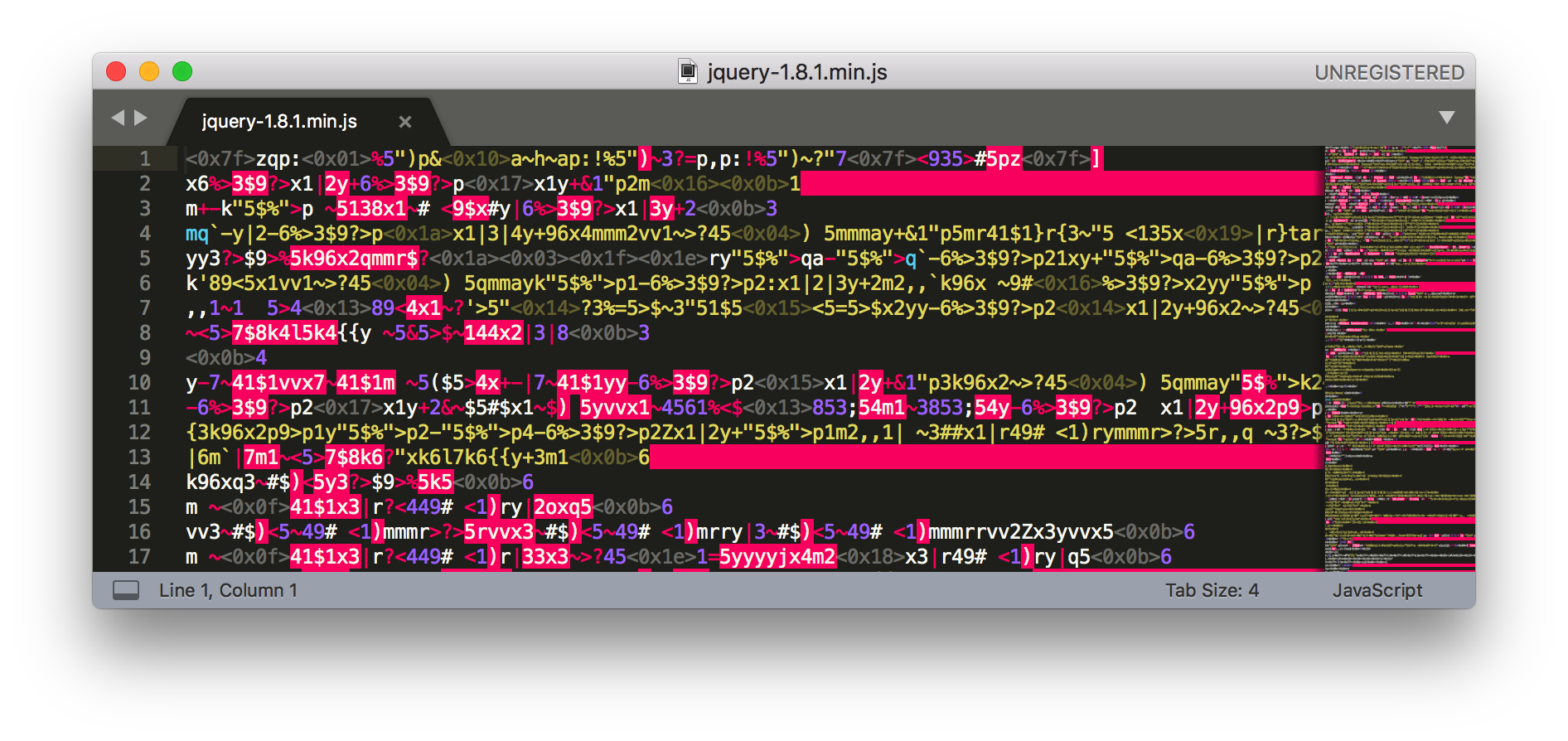
2.5 Game related protection
Provide all-round protection through the anti-tampering and encryption of script/dll files used by mainstream game engines
With game-related protection, it's impossible to get the plaintext script or plaintext dll file

2.6 Local data protection
All-round protection of local data files through anti-tampering and encryption
With local data protection, it's impossible to get plaintext db file or sp file
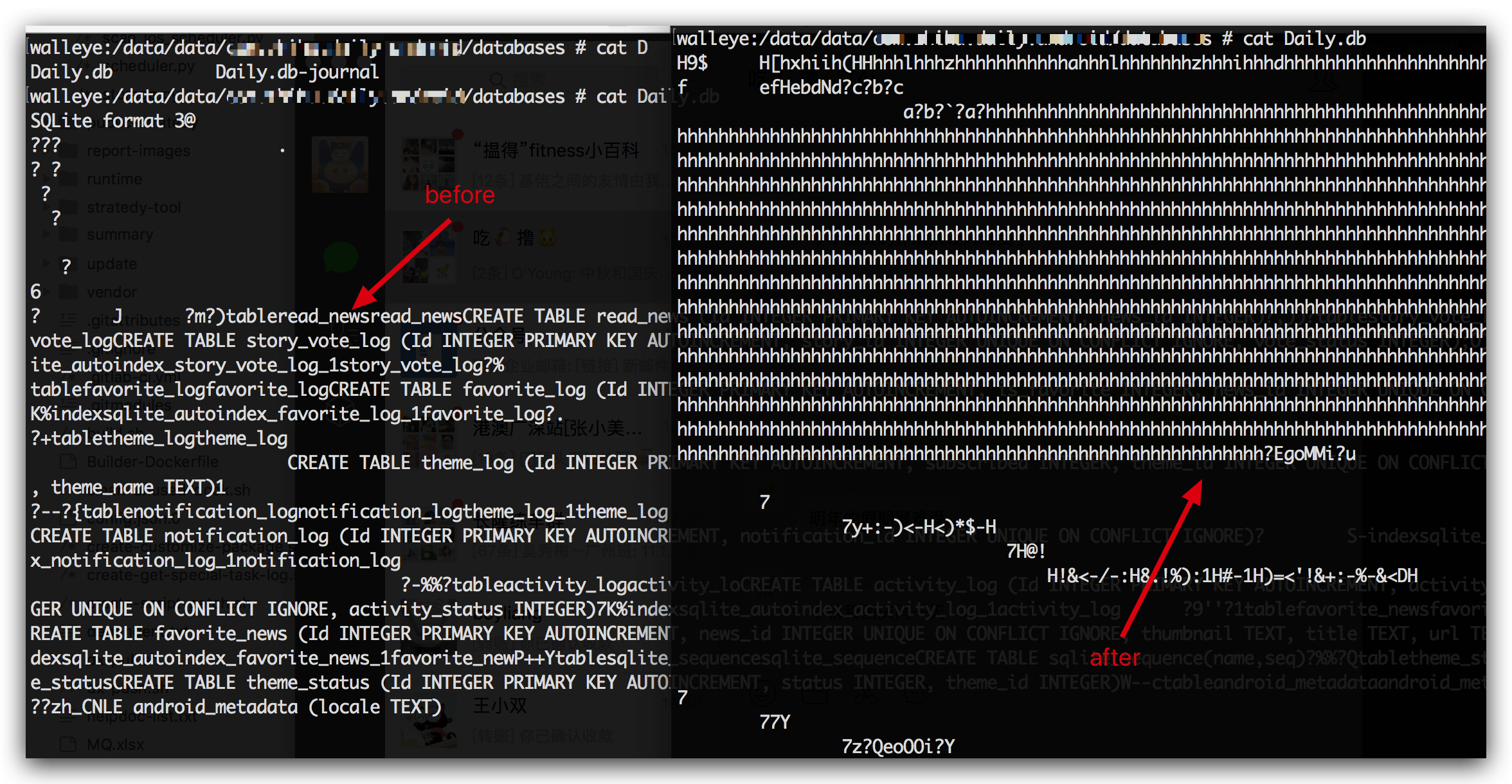
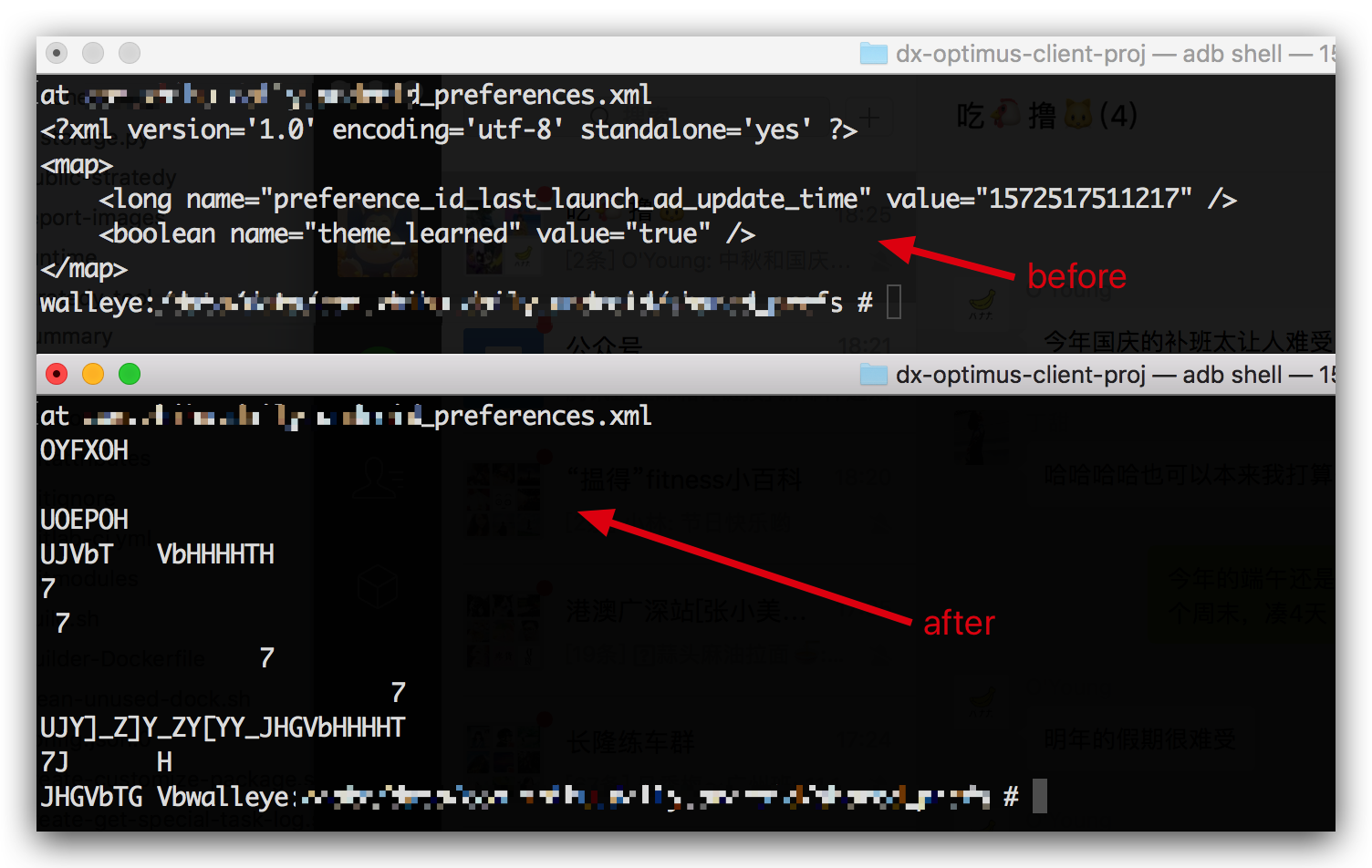
2.7 Runtime protection
With runtime protection, behaviors such as debugging, memory dumping, and code injection are prevented.
3. Scope of application
- Android versions: 4.2+
- Languages: java, kotlin
- Formats:
- App,
.apkformat,.aabformat - skd,
.aarformat,.jarformat
- App,
- Other requirements:
- apk package must contain signature
- apk files must not be processed with defense
- The size after compression is under
2048M
4. Operating guide
4.1 Preparation of document to be defensed
- Prepare the signed apk file to be processed.
- Prepare the same signature key file as the apk file to be processed.
4.2 Upload defense files
4.2.1 Base version
- Login AISecurius control panel, and enter Android defense page
- Select base version, and click Apply, the Create window pops up, and upload apk to be processed
- Click OK to create a task
4.2.2 Standard version
- Login AISecurius control panel, and enter Android defense page
- Select Standard version, and click Apply, the Create window pops up, and upload apk to be processed
- Select defense strategy as needed
- Standard: It protects common android applications, including dex file encryption, dexvmp, anti-tampering, anti-debugging, anti-memory dump, anti-injection, and app package signature verification.
- html/js: Encrypt html, js and other files, and other functions include anti-tampering, anti-debugging, app package signature verification, anti-memory dump, and anti-injection.
- Level protection: Level protection tailored as needed.
- Game: Encrypt game engine script files such as u3d and cocos2dx, it also includes anti-tampering, anti-debugging, anti-memory dump, anti-injection, and app package signature verification.
- Click OK to create a task
4.2.3 Professional version
- Login AISecurius control panel, and enter Android defense page
- Contact the customer service staff, explain the specific needs of the professional version, and wait for the configuration strategy to be completed
- Select professional version, and click Apply, the Create window pops up, and upload apk to be processed
- Click OK to create a task
4.3 Download the defense package
- After submitted, it will enter the waiting list. After the background processing is completed, you can download it from the task list.
- After downloaded, you will get the unsigned defense package in the same format as the source package, which is compressed package ended as .apk.
- The apk is ready to be used after re-signing it, which must be consistent with the signature before.
- If the defense fails, click "View Failure Reason" on the right side of the task list to check the reason.
5. Android signature
| Version | File | Remark |
|---|---|---|
| Windows | apk_tool.exe | This version includes the Java runtime environment and no additional installation is needed. |
| Universal version | AS-signer.jar | Please note that this version runs in Java 8+ operating environment. |
This tool is open source according to the Apache 2.0 protocol. View the source code here
5.1 Operating guide
- Download the AISecurius signature tool
dx-signer.jarand double-click to run. - Select the input apk, aab file.
- Select the signed key file and enter the key password.
- Select the path of apk and aab after re-signing that ends with apk. For example:
D:\sign.apk - Click the "Sign" button and wait until the signature is completed.
ps: If there is an alias (certificate alias) key or there are multiple certificates, please select alias in the advanced tab and enter the alias password