Device Fingerprinting User Manual
1 Quick Start Guide
1.1 Product Introduction
AISecurius Device Fingerprinting can generate a unique identification for the device based on the characteristic information such as hardware, network and environment of the network device of the user, covering Android, iOS and Web, so as to effectively detect risks such as simulator, simulation, Root, jailbreak, hijacking and injection, etc. Combined with AISecurius risk control system, it can effectively confront malicious behaviors such as device counterfeiting, automatic registration and seeking extra profits.
1.2 Names and Definitions
| Name | Interpretation |
|---|---|
| AppId | The public key is a 32-bit character string, which is the unique identification for access to the channel. After service is open, it may be obtained from the secondary menu "application management" of device fingerprint. Appld can be used when the client is connected. |
| AppSecret | The private key is a 32-bit character string and the counterpart of the public key. After service is open, it may be obtained from the secondary menu "application management" of device fingerprint. Please keep it properly and never disclose it to others. AppSecret can be used when the user is inquiring device details. |
| token | As an identification returned after Device FingerprintingSDK is collected and reported. Token is not a device fingerprint, but the user may inquire the Device Fingerprintingvia token. |
| hardId | Device Fingerprinting |
| Front-end user | Web client or Android client and iOS client which integrates SDK |
| Back-end user | It refers to the background server of an enterprise. Explanation of nouns. |
Notes for developers:
| Quickly develop and use Appld | Exclusive Appld |
|---|---|
| The development and test interface connection is available: AppId: d7eb51437ed189ae6a42ef3cccf69cec | Please log in and get your exclusive Appld |
| Disadvantages: It is shared by multiple users and statistical data query cannot be implemented. | Advantages: The user can inquire statistical data and risk labels through graphic interface on the console. |
1.3 Interaction process
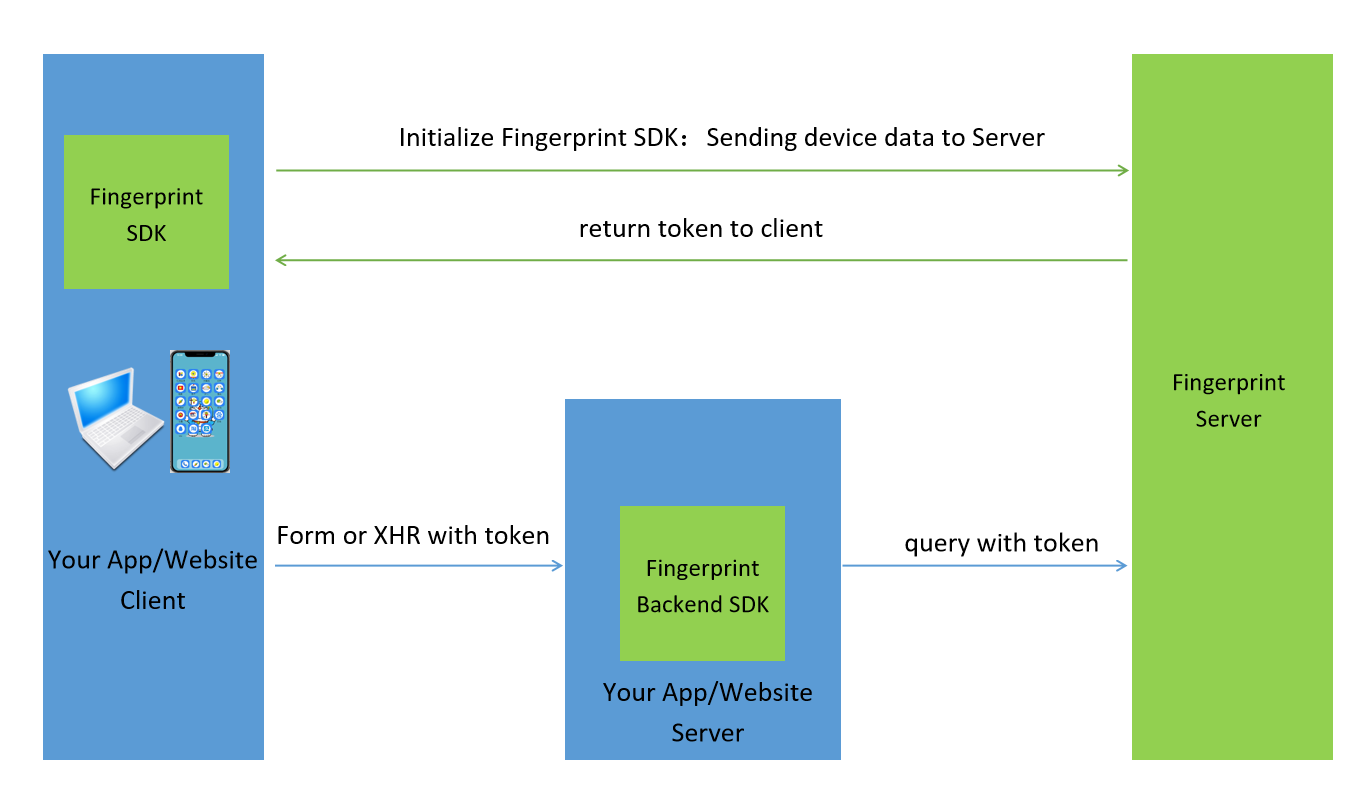
The call process for a single use of AISecurius Device Fingerprinting
- For client access, the business client needs to integrate AISecurius fingerprint client SDK, including Android, iOS, H5, etc. The user can obtain Device Fingerprintingtoken via AISecurius client SDK (note: token is not the device fingerprint).
- For business interface expansion, the business client needs to obtain Device Fingerprintingtoken if required via the corresponding api. The business interface needs to upload the fingerprint token obtained from the front end to the background.
- For background access, AISecurius will provide background SDK to inquire device details. SDK involves Java, PHP, etc.
Important: Due to such factors as the device network environment and device vision of the end user, the acquisition rate of Device Fingerprintingmay not to 100%, and a very few fingerprints may not be collected. Therefore, during fingerprint service integration, please do not strongly depend on fingerprint information.
2. Front End Access
- It supports Web access and mainstream browsers such as IE8+, Chrome, Firefox, 360 browser, QQ browser, as well as built-in Webview on Android and iOS. For the introduction of JS, see the chapter of Web access.
- It supports Android access, SDK acquisition and access. See the chapter of Android access.
- It supports iOS access, SDK acquisition and access. See the chapter of iOS access.
2.1 Web Access
Step 1: Introduction
Introduce const-id.js to HTML on the web, and the codes are as follows:
<script src="https://cdn.aisecurius.com/ctu-group/constid-js/as.js"></script>
Step 2: Generate and use
After page loading, initialize device fingerprint. It is necessary to call as.ConstID(options, callback) in JavaScript and obtain Device Fingerprinting token. The codes are as follows:
var options = {
appId: '[Enter AppID here]', // unique identification, service interface required
server: 'https://constid.aisecurius.com/udid/c1', // constId url, optional
userId: '[Enter userID here]' //user identification, optional
};
as.ConstID(options, function (err, token) {
if (err) {
// console.log('error: ' + err);
return;
}
// console.log('const-id token is ' + token);
});
It also supports Promise
as.ConstID(options).then(function(token) {
console.log(token)
}).catch(function(err) {
console.log(err)
})
Description of options field
| Field | Type | Required or not | Description |
|---|---|---|---|
| appId | String | Yes | Currently used identification |
| server | String | No | constId service interface, optional. If you do not enter it, the cloud service interface will be used in default. |
| scene | String | No | Scenario identification, such as login, survey, etc. |
| userId | String | No | The unique identification of the service provider, such as user name, user ID, phone number, Email, etc. |
| timeout | number | No | Time-out period, in ms |
| cache | boolea | No | It is true in default, representing caching collection results; If it is changed as false, a new collection is required each time. |
PC browser is compatible with
| Browser | The lowest version |
|---|---|
| IE | 9 |
| Edge | 20 |
| Chrome | 60 |
| Safari | 11 |
| Firefox | 60 |
The mobile browser is compatible with
| Browser | The lowest version |
|---|---|
| Chrome | 60 |
| Safari | 11 |
| UC | 12 |
| Native | Android 4.0 and above |
2.2 Android Access
I. Environmental requirements
| Entries | Description |
|---|---|
| development objectives | Android 5.0-13.x, 14.0 |
| CPU architecture | armeabi-v7a arm64-v8a x86 x86_64 |
II. Integrated SDK
2.1 Download SDK
Click to download demo (only used for code configuration demonstration. Please apply for appld at AISecurius background, and SDK needs to be replaced by the SDK downloaded from the link)
2.2 Android Studio integration
The content integration of SDK includes:
- dx-risk-vx.x.x.aar
2.2.1 Put aar file under the directory "libs" of corresponding module
2.2.2 Make the following configuration in build.gradle of such Module:
android{
sourceSets {
main {
jniLibs.srcDirs = ['libs']
}
}
packagingOptions {
doNotStrip "**/libDX*.so"
}
}
repositories{
flatDir{
dirs 'libs'
}
}
dependencies {
implementation fileTree(dir: 'libs', include: ['*.aar'])
}
2.3 Add permissions required for SDK
<!-- Required-apply in default -->
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.ACCESS_WIFI_STATE"/>
<!-- Optional-dynamic application is required for version 6.0 and above -->
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE"/>
<uses-permission android:name="android.permission.READ_PHONE_STATE"/>
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION" />
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION" />
<uses-permission android:name="android.permission.ACCESS_BACKGROUND_LOCATION"/>
<uses-permission android:name="android.permission.BLUETOOTH"/>
2.4 Confused configuration of Proguard
-dontskipnonpubliclibraryclassmembers
-keepattributes *Annotation*,EnclosingMethod
-dontwarn com.dx.mobile.**
-dontwarn *.com.dx.mobile.**
-dontwarn *.com.mobile.strenc.**
-keep class com.dx.mobile.risk.**{*;}
-keep class com.security.inner.**{*;}
-keep class *.com.dx.mobile.**{*;}
-keep class *.com.mobile.strenc.**{*;}
2.5 Description of dynamic application for API 6.0 permissions and above
Permissions which require dynamic application are as follows:
android.permission.WRITE_EXTERNAL_STORAGE
android.permission.READ_EXTERNAL_STORAGE
android.permission.READ_PHONE_STATE
android.permission.ACCESS_COARSE_LOCATION
android.permission.ACCESS_FINE_LOCATION
Cases of dynamic code application (under Activity):
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
setContentView(R.layout.activity_demo);
// Dynamic application of API 23 permissions and above
if (Build.VERSION.SDK_INT >= Build.VERSION_CODES.M) {
String[] permissionArray = {
"android.permission.ACCESS_COARSE_LOCATION",
"android.permission.ACCESS_FINE_LOCATION",
"android.permission.ACCESS_BACKGROUND_LOCATION",
"android.permission.WRITE_EXTERNAL_STORAGE",
"android.permission.READ_EXTERNAL_STORAGE",
"android.permission.READ_PHONE_STATE",
};
this.requestPermissions(permissionArray, 1);
}
}
@Override
public void onRequestPermissionsResult(int requestCode, String[] permissions, int[] grantResults) {
super.onRequestPermissionsResult(requestCode, permissions, grantResults);
// start getToken
new Thread(new Runnable() {
@Override
public void run() {
HashMap<String, String> params = new HashMap<String, String>();
String token = DXRisk.getToken("appid", params);
}
}).start();
}
III. Description of interface use
3.1 Description of methods and parameters
Function description
The Device Fingerprinting information from the collection end is uploaded to the risk control backend, which then returns a token. This API is time-consuming and must be called on a non-main thread, otherwise an exception will be thrown.
Description of methods
DXRisk.java is the interface for risk control module of DxRisk SDK, which collects local information and returns token from the user end.
Initiation setup
It is necessary to call setup before using SDK. Setup is mainly used to initiate data/environment, which is usually called under onCreate of Application:
/**
* Initiation parameters and environment
* @param context
* @return
*/
public static boolean setup(Context context)
PS: There is no difference in the following two methods for obtaining token in case of unobstructed network.
Conventional Token
/**
* @return token It usually returns a 40-bit character string. In case of obstructed or blocked network, it returns a 4-5k character string.
* @throws DXRiskErrorException If the user calls this API from the main thread or appld is void, then it will indicate an abnormal status.
*/
public static String getToken(String appId, HashMap<String, String> paramsMap) throws DXRiskErrorException
Simplified Token
The device information that light-weight token can obtain is far less than getToken(). As a result, a big error may occur when the user is judging whether the device is at risk. Please use it with caution.
/**
`* @return token It usually returns a 40-bit character string. In case of obstructed or blocked network, it returns a 1k character string. 。
`* @throws DXRiskErrorException, If the user calls this API from the main thread or appld is void, then it will indicate an abnormal status.
*/
public static String getLightToken(String appId, HashMap<String, String> paramsMap) throws DXRiskErrorException
3.2 Examples
3.2.1 Initiation setup
It is recommended to call under Application.onCreate
@Override
public void onCreate() {
super.onCreate();
// Environment initialization
DXRisk.setup(this);
}
3.2.2 Acquisition of token
The entire process is operated in a long-running way. Therefore, the execution is a must on the non-main thread. Otherwise, crash will occur.
new Thread(){
@Override
public void run() {
HashMap<String, String> params = new HashMap<String, String>();
// Fill in the corresponding server url here.
params.put(DXRisk.KEY_URL, "https://constid.aisecurius.com");
// Set up the timeout of token request. If not set, it is 500ms by default
params.put(DXRisk.KEY_DELAY_MS_TIME, "2000");
// This configuration disables the SDK cache, indicating that information is forcibly collected every time the interface is invoked
// params.put("PRIVATE_CLEAR_TOKEN", "clear");
// It is possible to acquire token from the application management menu after the service is available.
String appId = "XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX";
// acquire the Device Fingerprinting token
final String token = DXRisk.getToken(appId, params);
// TODO, and upload token to the user back-end through Post request
}
}.start();
3.3 Exception specification
While acquiring the token, the interface may return as null in case of network timeout or failure in encryption and decryption, and an error message with the tag of DXRISK will be output at the same time, as detailed below
DXRISK_REQUEST_NETWORK_ERR -1001 // Network linking failure
DXRISK_REQUEST_DECRYPT_ERR -1002 // data decryption error
DXRISK_REQUEST_UNCOMPRESS_ERR -1003 // decompression error
DXRISK_REQUEST_RESPONSE_EMPTY_ERR -1004 // return as null
DXRISK_REQUEST_DATA_PARSE_ERR -1005 // data analysis
DXRISK_REQUEST_DIRTY_DATA_ERR -1006 // dirty data
DXRISK_CONST_ID_EMPTY -1007 // constid is empty
Contact the technicians of AISecurius for any of the above error messages.
2.3 iOS Access
I. Environment Requirements
| Entry | Description |
|---|---|
| compatible platform | iOS 8.0+ |
| development environment | XCode 4.0 + |
| CPU architecture | armv7, arm64, i386, x86_64 |
| SDK dependence | libz, libresolv, libc++ , SystemConfiguration.framework , CoreLocation.framework , CoreTelephony.framework |
II. Integrated SDK
2.1 Download SDK
Click to download the integrated oc version of demo
Click to download the integrated swift version of demo
Click to download the fingerprint SDK
The catalog structure of the SDK is as follows:
dx-risk-iOS-x.x.x-xxxxxxxCatalog DXRisk sdk- DXRisk.framework Dynamic Library Framework without idfa acquisition logic
- DXRiskWithIDFA.framework Dynamic Library Framework with idfa acquisition logic
- DXRiskStatic.framework Static Library Framework without idfa acquisition logic
- DXRiskStaticWithIDFA.framework Static Library Framework with idfa acquisition logic
2.2 SDK access to XCode
2.2.1 Import of Framework
DXRisk.framework,DXRiskWithIDFA.framework,DXRiskStatic.framework,DXRiskStaticWithIDFA.framework Drag one of them directly into the project catalog, or right click the general folder to add a file.
If the App has advertising-related functions, select DXRiskWithIDFA.framework or DXRiskStaticWithIDFA.framework, which will provide the more accurate token
In case of no advertising, obtaining idfa may result in the rejection of update. Then, select DXRisk.framework or DXRiskStatic.framework
2.2.2 Addition of FrameWork to project
To add DXRisk.framework or DXRiskWithIDFA.framework to the project, select Target -> General. In Frameworks, Libraries, and Embedded Content, switch the Embed corresponding to DXRisk.framework or DXRiskWithIDFA.framework to Embed & Sign. As illustrated in following figure:
To add DXRiskStatic.framework or DXRiskStaticWithIDFA.framework to the project, set -ObjC in Build Settings -> Other Linker Flags, as shown in the following figure:
2.2.3 Configuration of packaging scripts
The following operations are only limited to the import of DXRisk.framework, DXRiskWithIDFA.framework dynamic library
This step will mainly solve the inconformity with the architecture of uploading Store. If Carthage has been configured in the project or there are other relevant packaging Framework adjustment scripts, skip this step and make adjustment. Select Target -> Build Phases, click "+" button, and add the following script:
APP_PATH="${TARGET_BUILD_DIR}/${WRAPPER_NAME}"
# This script loops through the frameworks embedded in the application and
# removes unused architectures.
find "$APP_PATH" -name '*.framework' -type d | while read -r FRAMEWORK
do
FRAMEWORK_EXECUTABLE_NAME=$(defaults read "$FRAMEWORK/Info.plist" CFBundleExecutable)
FRAMEWORK_EXECUTABLE_PATH="$FRAMEWORK/$FRAMEWORK_EXECUTABLE_NAME"
echo "Executable is $FRAMEWORK_EXECUTABLE_PATH"
EXTRACTED_ARCHS=()
for ARCH in $ARCHS
do
echo "Extracting $ARCH from $FRAMEWORK_EXECUTABLE_NAME"
lipo -extract "$ARCH" "$FRAMEWORK_EXECUTABLE_PATH" -o "$FRAMEWORK_EXECUTABLE_PATH-$ARCH"
EXTRACTED_ARCHS+=("$FRAMEWORK_EXECUTABLE_PATH-$ARCH")
done
echo "Merging extracted architectures: ${ARCHS}"
lipo -o "$FRAMEWORK_EXECUTABLE_PATH-merged" -create "${EXTRACTED_ARCHS[@]}"
rm "${EXTRACTED_ARCHS[@]}"
echo "Replacing original executable with thinned version"
rm "$FRAMEWORK_EXECUTABLE_PATH"
mv "$FRAMEWORK_EXECUTABLE_PATH-merged" "$FRAMEWORK_EXECUTABLE_PATH"
done
2.2.4 Permission precautions
In the iOS 12, it is the best to start in Capabilities->Access WiFi Information, which is convenient for the Device Fingerprintingdata acquisition.
III. Description of interface use
3.1 Description of methods and parameters
// The risk control module:DXRiskManager
@interface DXRiskManager : NSObject
// string constant
extern NSString* const DXRiskManagerKeyUserId;
extern NSString* const DXRiskManagerKeyEmail;
extern NSString* const DXRiskManagerKeyPhone;
extern NSString* const DXRiskManagerKeyUserExtend1;
extern NSString* const DXRiskManagerKeyUserExtend2;
extern NSString* const DXRiskManagerKeyDegradeNotify; // if the data degrading notice is enabled, the corresponding degrading statistics are available at the server
extern NSString* const DXRiskManagerKeyCountry; // the national and regional settings, It is "China" by default
extern NSString* const DXRiskManagerKeyDelayMsTime; // Fill in and set the request timeout (ms) (500 by default, with a range of [100: 3, 000])
// NoticeDegrade parameters
/* The NoticeDegrade Value. This value only be used pair with key:DXRiskManagerKeyDegradeNotify to notify token degrade. */
extern NSString* const DXRiskManagerKeyDegradeNotifyEnable;
// Backup parameters
/* The Backup Value. This value only be used pair with key:DXRiskManagerKeyBackup to set data backup. */
extern NSString* const DXRiskManagerKeyBackupEnable;
// Country parameters
/* The Country Value. This value only be used pair with key:DXRiskManagerKeyCountry to set country. */
extern NSString* const DXRiskManagerCountryChina;
/* The Country Value. This value only be used pair with key:DXRiskManagerKeyCountry to set country. */
extern NSString* const DXRiskManagerCountryIndonesia;
/**
Device Fingerprintinginformation at the acquisition end, which are uploaded to the risk control background. Then, the risk control background returns token.
It is a long-running operation for this API. Therefore, it must be called on the non-main thread.
@param appId appId After the service is available, the configuration items and initialization methods can be obtained in the secondary menu, "Application Management"
@param extendsParams
@return token
*/
+ (NSString *)getToken:(NSString *)appId extendParams:(NSDictionary *)extendsParams;
/**
DXRiskManager -- initialize method
*/
+ (BOOL)setup;
@end
3.2 Examples
// The entire process is operated in a long-running way. Therefore, the execution is a must on the non-main thread. Otherwise, UI will be blocked. If it is already executed on a non-UI thread, another thread is not required
dispatch_queue_t dxrisk_queue = dispatch_queue_create("dx-risk", DISPATCH_QUEUE_CONCURRENT);
dispatch_async(dxrisk_queue, ^{
NSMutableDictionary *dic = [NSMutableDictionary dictionary];
// According to business logic, fill in the custom fields.
[dic setObject:@"123456" forKey:DXRiskManagerKeyUserId];
[dic setObject:@"https://constid.aisecurius.com" forKey:DXRiskManagerKeyURL];
// The parameter is the backup Appid provided by the backup database of AISecurius, and then the following notes
// [dic setObject:@"clear" forKey:@"PRIVATE_CLEAR_TOKEN"];
// acquisition token
// Note: It is the best not to save the token in a local variable or field. It is obtained through API for use each time.
BOOL isSuccess = [DXRiskManager setup];
NSLog(@"setup success: %@" , isSuccess ? @"YES":@"NO");
NSString *constID = [DXRiskManager getToken:@"xxxxxxxxxxxxxxxxxxxx" extendsParams:dic];
NSLog(@"constID: %@", constID);
// TODO uploads the constid to the business background through the Post request.
// The process of simulating the frequent calls is as follows.
while(TRUE) {
NSLog(@"constID: %@", [DXRiskManager getToken:@"xxxxxxxxxxxxxxxxxxxx" extendsParams:dic]);
[NSThread sleepForTimeInterval:.5];
}
});
3.3 Exception specification
While acquiring the token, the interface may return as null in case of network timeout or failure in encryption and decryption, and an error message with the tag of DXRISK will be output at the same time, as detailed below:
DXRISK_REQUEST_NETWORK_ERR -1001 // network connect failure
DXRISK_REQUEST_DECRYPT_ERR -1002 // data decryption error
DXRISK_REQUEST_UNCOMPRESS_ERR -1003 // decompression error
DXRISK_REQUEST_RESPONSE_EMPTY_ERR -1004 // return as null
DXRISK_REQUEST_DATA_PARSE_ERR -1005 // parse data error
DXRISK_REQUEST_DIRTY_DATA_ERR -1006 // dirty data
DXRISK_CONST_ID_EMPTY -1007 // constid is empty
Contact the technicians of AISecurius for any of the above error messages.
3. Back-end Access
Detailed description of interface: Obtain the device information based on three parameters, i.e. token, appId and sign
3.1 Description of SDK access methods
1.1 Java SDK access
Package introduction
<dependency>
<groupId>com.aisecurius</groupId>
<artifactId>ctu-client-sdk</artifactId>
<version>2.6</version>
</dependency>
Java example
public class ConstantIdDemo {
// You can acquired appId and appSecret from the Device Fingerprintingmenu application management in the console of AISecurius.
private static String appId = "0091a3xxxxxxxxxx557fac67b2f5afb";
private static String appSecret = "e38dxxxxxxxxx6807c9e1edebaa2836";
public static void main(String[] args) throws IOException {
// Fill in the Device Fingerprinting domain
CtuConstidClient client = new CtuConstidClient("https://constid.aisecurius.com", appId, appSecret);
// Device Fingerprinting
String result = client.getDeviceInfo("62c5013cel9o4xxxxxxxxxtTtKW5BwWtQq9u1f1");
System.out.println(JSON.toJSON(result));
}
}
1.2 PHP SDK access
Use the example
class Demo {
// Enter the value based on the actual situation
const appKey = "your AppID";
// Enter the value based on the actual situation
const appSecret = "your AppSecret";
// Enter the value based on the actual situation
const token = "token obtained from the SDK";
}
// obtain the detailed information of devices based on token
$requestHandle = new DeviceFingerprintHandle();
// set the request timeout of tools. 2s is set by default since the Device Fingerprinting degrading and network jitter exist. It is allowed to make adjustment
// $requestHandle->setTimeout(2);
// fill in the Device Fingerprintingdomain name or url, example:http://127.0.0.1:9090
$responseData = $requestHandle->getDeviceInfo("https://constid.aisecurius.com/udid/api/getDeviceInfo",
Demo::appKey, Demo::appSecret, Demo::token);
$result = json_decode($responseData, true);
// request the status code according to the actual situation. If it is not 200, it indicates that the detailed information of device is not obtained
if ($result['stateCode'] == 200)
echo "The detailed information of device is as follows: : " . json_encode($result['data'], true);
else
echo $result['message'];
1.3 NodeJS SDK
npm i dx-const-id-sdk --save
const SDK = require('dx-const-id-sdk')
const sdk = new CaptchaSDK({
appId: 'your appId',
appSecret: 'your appSecret'
})
sdk.getDeviceInfo(token).then((data) => {
console.log(data)
}).catch(err => {
console.log('Failed to obtain device information')
})
3.2 HTTP interface access methods
2.1 Request parameters
| Field | Type | Description |
|---|---|---|
| appId | String | Currently used identification |
| sign | String | sign = MD5(appSecret + token + appSecret), AppSecret is the secret key corresponding to appId |
| token | String | token acquired from the front end of user |
2.2 Successful response
| Field | Type | Description |
|---|---|---|
| stateCode | int | Status code |
| message | String | Status description |
| data | Json | Return the device information and device risk test data |
{
"stateCode": 200,
"message": "Request for response succeeds ",
"data": {
"hardId": "22e38229a7eda501c58bf3ddee1a340a",
......
}
}
2.3 Error response
| Field | Type | Description |
|---|---|---|
| stateCode | int | Status code |
| message | String | Status description |
| data | Json | Data is null if an exception occurs |
{
"stateCode": -10002,
"message": "The signature is null or verification fails ",
"data": null
}
| Error code | Description |
|---|---|
| -10001 | appId does not exist or has expired |
| -10002 | The signature is null or verification fails |
| -10003 | The token is null, or there is no corresponding device information |
| -10004 | token has expired |
| -10005 | Internal error of server |
| -10006 | Certificate has expired |
| -10007 | Traffic limiting of server |
3.3 Description of detailed return parameters of HTTP interface
3.1 Free user
| Field name | Field description |
|---|---|
| token | Device token |
| hardId | Device Fingerprinting |
3.2 Charged user
3.2.1 Mobile end return results (some examples are shown. Contact the after-sales support staff to obtain more return fields)
| Field name | Field description |
|---|---|
| token | Device token |
| deviceType | Device type |
| hardId | Device Fingerprinting |
| producter | Manufacturer |
| macAddress | MAC address |
| isEmulator | Simulator operation |
| isRoot | root or not |
| isMultirun | Multi-operation or not |
| isInject | Injection risk existing or not |
| isMemdump | dump risk of memory existing or not |
| isDebug | Debugging risk existing or not |
| isHook | hook risk existing or not |
| isJailBreak | Jailbreak or not |
| isVpn | Use of vpn or not |
| isProxy | Use of agency or not |
| isSimulateGPS | Tampering of GPS or not |
| isCloudPhone | Cloud real machine or not |
3.2.2 web end return results (some examples are shown. Contact the after-sales support staff to obtain more return fields)
| Field name | Field description |
|---|---|
| token | Device token |
| deviceType | Device type |
| hardId | Device Fingerprinting |
| canvasId | canvas fingerprint |
| webGl | WebGl fingerprint |
| resolution | Device resolution |
| isLiedBrowser | Counterfeit of browser or not |
| isCookieDisabled | Disabling of cookie or not |
| isTamperUa | Tampering of browser ua or not |
| isTamperRes | Tampering of resolution or not |
| isTamperCd | Tampering of browser color depth or not |
| isEmulator | Simulator or not |
4. Appendix: Example of Privacy Policy
It is recommended to add the Privacy Policy Statement for the apps integrating SDK to avoid risks. Besides, sdk is called after the customer agrees with the privacy policy. The example is as follows:
Privacy policy (drafted, and it can be modified according to the actual situation)
4.1 How Do We Collect and Use Personal Information
Personal information refers to all kinds of information which is recorded electronically or in other forms, able to identify the identity of a specific natural person or reflect the activities of a special natural person independently or in combination with other information. We know the importance of personal information to you very well, and your trust is very important to us. We will strictly follow the laws and regulations to take safety precautions accordingly to be devoted to protecting your personal information security under control. We will only collect and use your personal information for the following purposes as mentioned in this policy:
- When you are using XXX product and related services, in order to guarantee the normal operation of software and services, we will collect your information, including hardware model, operating system version number, international mobile equipment identity (IMEI), network device hardware address (MAC), IP Address, software version number, network access method and type, and operation logs. Please understand that such information is basic that we must collect for us to provide services and guarantee the normal operation of products.
| System | Third-party | Purpose of personal information collection by third party | Scope of personal information collection by third party | Methods of personal information collection by third party |
|---|---|---|---|---|
| iOS | Device FingerprintingSDK | Identify the devices, to guarantee the security of accounts and transactions | Device version, system version, generated ID, mobilephone style, and mobilephone name | Automatic collection, and collection when starting the APP and initializing the SDK |
| Android | Device FingerprintingSDK | Identify the devices, to guarantee the security of accounts and transactions | Device version, system version, generated ID, mobilephone style, mobilephone name, iccid, bssid, MAC address, IMSI and IMEI | Automatic collection, and collection when starting the APP and initializing the SDK |
- Services of cookies and similar technologies Cookies and similar device information identification technology is commonly used on the Internet. While you are using our services, we may send one or more Cookies or anonymous identifiers (hereinafter referred to as "Cookie") to your devices by related technologies, so as to collect, identify and save the information when you visit and use this product. We promise not to use Cookie for any purpose other than those described in this Privacy Policy. Our use of Cookie mainly aims at guaranteeing the safe and efficient operation of products and services, checking the abnormalities related to crashes and delays, and assisting you in avoiding the repetition of the steps and processes to fill in the forms and enter the content to be searched. In the meantime, we may use Cookie to show you the information or features in which you may be interested and to optimize your advertising choices. The function of clearing the browser caches in most of browsers is available for users. You may clear the data accordingly, or revise the acceptance to Cookie, or refuse our Cookie. The Cookie-dependent services or corresponding functions may not be available due to these modifications.
Appendix: Relevant definitions Personal information: refers to all kinds of information recorded by electronic or other methods or related to recognized or recognizable natural person, excluding the information subject to anonymous processing. Device information: including device identifiers (IMEI, IDFA, Android ID, MAC, OAID, IMSI and other device-related information), device parameters and system information (device type, device model, operating system and hardware-related information), and device network environment information (IP address, WiFi information, base station information and other network-related information). The actually collected information of product shall prevail.
4.2 How do we protect your personal information
(I) We have taken the security protection measures in line with the industry standard to protect your personal information, preventing the data from unauthorized access, public disclosure, use, modification, damage or loss. We will take all the reasonable and feasible measures to protect your personal information. For example, the SSL encipherment protection is applied at the time of data exchange between your browser and "service"; we also provide a secure browsing way (https) on our website; we will use the encryption technology to ensure the data confidentiality; we will prevent the data from malicious attack based on the trusted protection mechanisms; we will deploy the access control mechanism to ensure that only authorized personnel can access the personal information; and we will organize the training courses of security and privacy protection, to intensify the understanding of staff on the importance to protect personal information.
(II) We will take all reasonable and practical measures to ensure that no irrelevant personal information is collected. We will only retain your personal information within such period as needed to achieve the purpose described in this Policy unless otherwise required for an extended retention period or permitted by law.
(III) The Internet is not an absolutely secure space, and email, instant messaging and other communication methods of our users are not encrypted. Therefore, we strongly recommend that you should not send personal information by such means. Please use a complex password to help us ensure your account security.
(IV) Although the Internet environment is not 100% secure, we will try our best to ensure or guarantee the security of any information sent to us by you. In the event that your legal interests are impaired by reason of unauthorized access, public disclosure, tampering or damage of your information incurred by destruction of our physical, technical or management protection facilities, we will undertake the relevant legal liability.
(V) In the event of any personal information security incident unfortunately, in accordance with the laws and regulations, we will immediately inform you of the followings: basic information and potential impact of security incidents, handling measures that we have taken or will take, recommendations for your prevention and reduction of risks, and remedial measures for you. We will immediately inform you of relevant circumstances of such incident by means of email, letter, call and push notification. If it is difficult to singly inform the subject of personal information, we will make an announcement by reasonable and effective means. At the same time, we will report the handling of personal information security incidents on our own initiative pursuant to the requirements of the regulatory department.