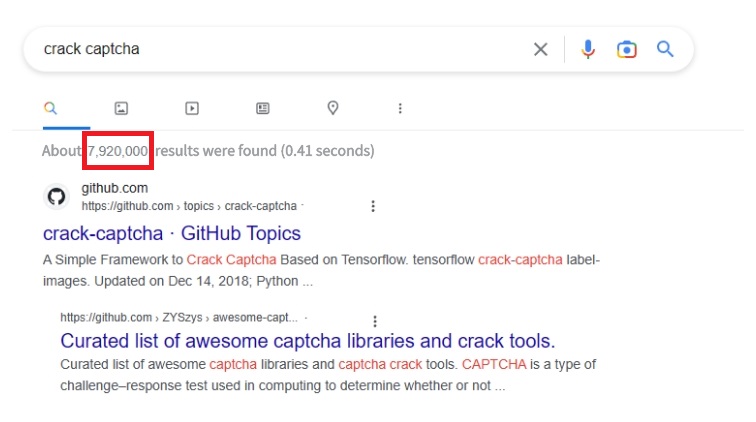
Enter the keyword "crack the verification code" online, and there will be 7,920,000 search results. "Verification code identification, easy cracking, brute force cracking, logical loophole cracking, simple cracking" and other keywords are endless, and there are even more posts about "how to crack a certain verification code with a certain method".
 As a key element that often appears in human-computer interaction interfaces, verification codes are an important component of identity verification and risk prevention, and are also the first gate of user interaction experience. They are widely used in services such as reading, education, finance, shopping, and government affairs.
As a key element that often appears in human-computer interaction interfaces, verification codes are an important component of identity verification and risk prevention, and are also the first gate of user interaction experience. They are widely used in services such as reading, education, finance, shopping, and government affairs.
The full name of the verification code is "Full-automatic Turing Test to Distinguish Computers and Humans". The core uses "human beings can easily identify text information in pictures with the naked eye" to distinguish the authenticity of the operator through identification, input, interaction, etc. It plays a huge role in various scenarios such as registration, login, transaction, and interaction. It can prevent operators from using machine software to program garbage registration, counterfeit login, steal information, swipe tickets and traffic, and ensure account security. important role.
Who wants to crack the verification code? Black and gray products
Heihui products are the people who most want to crack the verification code. By cracking the verification code, Heihui can steal data, steal personal information, and collect wool on a large scale.
In 2017, the Chinese police successfully cracked the country's first case of using AI (artificial intelligence) to commit crimes and violate citizens' personal information. The criminal suspect, Yang, trained the machine by using artificial intelligence machine deep learning technology, so that the machine can operate and identify autonomously like ALPHAGO, effectively identify the picture verification code, and easily bypass the verification code security policy set by the Internet company. The recognition system developed by it is very fast, and can recognize thousands of verification codes in a short time, and it is fast and accurate, and can recognize more than 98% of the verification codes.
The tool developed by Yang is dedicated to providing decoding services for black and gray products that steal and sell user information. That is to say, the black and gray production gangs need to "crash" the stolen data, "clean" the various associated accounts and passwords of the stolen information, and then make the victim's information more complete, so as to implement precise fraud. Yang used the system developed by himself to provide black and gray products with the verification code cracking when "crash database".
To be safe, the verification code must be better than black and gray production technology
No system is invulnerable, and neither is the captcha. What developers need to do is to increase the attack threshold, improve the anti-cracking ability, and enhance their own security, so that black and gray products feel that the input-output ratio is not worthwhile and give up.
The fifth-generation intelligent verification code launched by Aisecurius, based on data information such as user behavior and environmental information, combined with models and risk control analysis, provides multi-dimensional risk identification, integrates a variety of offensive and defensive confrontation combinations, and has 13+ verification methods of different difficulties. Cloud perception intelligence sharing, self-renewal and evolution capabilities, stronger offensive and defensive confrontation, and better user experience without perception can effectively prevent malicious cracking and prevent and control various business risk threats.
 In terms of anti-cracking and self-security, the fifth-generation smart verification code has five unique skills.
In terms of anti-cracking and self-security, the fifth-generation smart verification code has five unique skills.
Integrate behavioral algorithms to enhance operational protection. The fifth-generation smart verification code is identified through behavioral trajectory model detection, such as the sliding trajectory of the mouse in the page, the typing rate of the keyboard, the sliding trajectory, speed, and button click of the sliding verification code. At the same time, it uses Isolation Forest (Isolation Forest, an anomaly detection algorithm) to propose the concept of isolation, which isolates abnormal data from the existing data distribution to achieve the purpose of anomaly detection, which can not only effectively improve the performance of verification codes on machines , The ability to identify malicious behavior can enhance the protection of operations.
Integrated Verification Rubik's Cube to achieve active confrontation. The fifth-generation smart verification code uses technologies such as random cutting of pictures, regular processing of picture updates, and picture variation, combined with correlation detection to prevent, and judges correlation through built-in rules and strategies, such as the correlation of the same device and the same IP correlation, sliding failure correlation, verification times correlation, etc., to effectively identify abnormal correlations in a short period of time. In particular, the integrated verification Rubik's Cube can be configured within 10s and takes effect within 60s, enabling rapid offensive and defensive confrontation.
Embedded out-of-order transmission, effectively preventing hijacking. The fifth-generation smart verification code has a built-in "out-of-sequence cutting image transmission" function in the data transmission link, which can cut the background image out of order and then spread it.
Dynamic encryption and decryption to defend against known attacks. Aisecurius' fifth-generation intelligent verification code proprietary dynamic encryption and decryption obfuscation algorithm can obfuscate and compress JS code, automatically update the algorithm regularly, automatically change data encryption, realize rapid and automatic iteration of verification code verification, and greatly enhance the difficulty of cracking.
Man-machine training model to fight against unknown threats. Aisecurius' fifth-generation intelligent verification code integrates real-time stream computing and scene strategies, combines man-machine models trained by machine learning, and correlation analysis of historical data. Through graphic algorithms and AI models, machine learning modeling is performed on user-generated behavior trajectory data, combined with Multiple dimensional information such as access frequency, geographical location, and historical records can quickly and accurately return human-machine judgment results, resisting automatic identification of programs, and resisting attacks from new technologies.
Fifth Generation Smart Captcha is part of Aisecurius Defense Cloud
Captchas are improved in constant iterations of attack and defense. As part of the aisecurius defense cloud, the fifth-generation smart captcha has unique features of security intelligence, cloud policy and AI modeling, making it a step further in security verification and self-protection.
Aisecurius defense cloud is based on years of actual combat experience and technical products. It has rich technical tools, tens of thousands of security policies and hundreds of business scenario solutions. It has the capabilities of intelligence, perception, analysis, strategy, protection and disposal, and provides modular configuration. And flexible expansion, helping enterprises build an independent and controllable business security system quickly, efficiently and at low cost.