
The principle of sameness and struggle of contradiction applies to almost all offensive and defensive confrontations.
In the last issue, we published How to ensure the uniqueness of device fingerprints when hardware attributes are no longer used as the identifier of device fingerprints". In the article, we introduced the evolution of hardware ID as the basic attribute of device fingerprint - that is, when hardware attribute is no longer used as the unique attribute of device fingerprint, in order to ensure the uniqueness of device fingerprint needs to add more identification criteria and dynamic variable algorithm based on hardware ID, in fact, this is a typical example of attack and defense confrontation.
Let's take another example. For example, in the offensive and defensive confrontation of device fingerprinting, the black and gray industry must "disguise" itself in order to bypass the device fingerprint to carry out attacks. At this point, there are two main ideas for bypassing the black and gray industry.
-
How to turn a device into multiple devices. For example, in a swipe scenario, making the app repeatedly think it is a new phone and thus repeatedly receiving the newcomer bonus.
-
How to turn a device into another device. For example, in an authentication scenario, the attacker's phone is spoofed to the victim's phone, allowing the app to log into the victim's account and steal funds, user information, etc.
But there is a spear, there is a shield, black and gray industry bypass ideas naturally can not escape the "eyes" of security researchers.
Today, we will talk about the idea of offensive and defensive confrontation with the theme of Hook.
A first look at Hook technology
First, a brief introduction to Hook technology.
Hook technology is a technology widely used in computer offensive and defensive confrontation. It can monitor various event messages in the system or process and intercept messages sent to the target window for processing.
We can simply compare the person using Hook technology to an angler, and Hook technology is like his fishing gear, the events constantly passed in the system is like a swimming fish, the angler through Hook technology will catch the target events he wants (Hook technology is generally directional), then you can modify the events, and then let it run normally, to achieve the purpose of the technical staff. technology is often used in hotfixes online, API hijacking, software cracking and other technical operations.
For example, we commonly use mouse and keyboard, if your computer is Hooked, then it also means that any operation you do is in the hands of the other party.
Hook technology is not only applicable to x86 systems, but also to mobile platform systems based on simple instruction sets, such as cell phones and other devices. Among them, Hook technology for mobile devices mainly focuses on cell phones.
For Android Hook framework, there are three main categories, one is for Native layer, i.e. system layer Hook framework, using PLT/GOT Hook or inline-Hook framework, such as bhook, xhook, yahfa, etc., one is for Java layer Hook framework, such as Xposed, and one is more special Hook framework - Frida, which is designed for the full platform Hook framework for x86 \ x86_64 \ arm \ arm64 architecture of the system, Hook on the iOS side of the main technical implementation through the Frida framework, and Frida in Hook technology implementation on Android also has a lot of audience, but mainly still Xposed class framework, the main reason is that Xposed on Andorid stability is better, and features are easier to hide.

Next, we'll talk about how to use Hook for offensive and defensive confrontation with Xposed and two other Hook frameworks (Edxposed and Lsposed) that iterate on Xposed as the core.
How to do an attack without knowing its attack - how to do an attack with Hook technology?
With the iterative update of Android version, Xposed framework also iterated with the new Hook framework.

At present, the main Hook framework for the Android platform is based on Lsposed, we will use Lsposed to Hook Android applications to see how to use Hook to attack.
First, the normal use of Lsposed requires several pre-requisites.
- A phone capable of unlocking BootLoaderLock.
- Prepare the boot.img of your own phone system.
- Preparing the Lsposed module installation package with the Magisk installation package.
- A computer with ADB tools installed.
 After the above conditions are prepared, you are ready to install and use Lsposed.
After the above conditions are prepared, you are ready to install and use Lsposed.
Once the installation is complete, we can use Hook to carry out the attack.
The specific process is as follows.
1. Decompile and analyze the target app.
To get the fish on the hook you have to know the properties of the fish. So the first step to successfully install Hook is to decompile and analyze the target app. Here we use jadx-gui to decompile and analyze the app.

Using jadx-gui we can see the decompiled source code. As shown in the figure below, by decompiling the app we arrive at the action it wants to pass the Flag, but note that this information is an uncertain value and we need to verify it further.

As you can see from the verification, no matter how many times you click the button, it will only show "Do you really believe in flags when you click?". This message. So, the next step is to take control of our own "catching" process.
2、Write code plug-ins to attack the "weakness" of the target app
At this point, we need to write a Hook plugin, modify some of its parameters, and then you can directly obtain its already calculated MD5 value (MD5 is an encryption algorithm. Also known as: irreversible encryption algorithm. The MD5 value is the password of any file after encryption of the plaintext password, also known as "digital fingerprint", anyone who has made any changes to the file, its MD5 value is the corresponding "digital fingerprint" will change. (Any changes made to the file will result in a change in the MD5 value, the corresponding "digital fingerprint".) What is it.
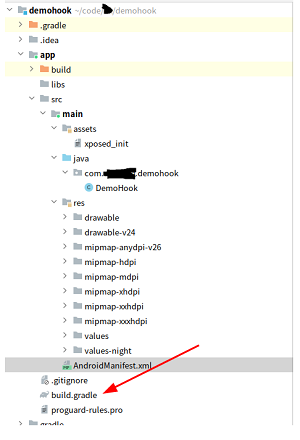
First we can use Android Studio or Idea with the Android plugin already installed, open a new project and select a project without an interface:

Note that when writing Xposed Hook modules, in order to be recognized by the Xposed framework, you need to create a file called xposed_init in your project's assets directory (if you don't have one, you can just create a new assets directory) and with the following contents for your package name + your main class name.


Next, open the AndroidManifest.XML file and fill it with the following content.


After configuring AndroidManifest.xml, we can start writing Xposed Hook module. The details are as shown in the figure.

In Xposed, there are two methods of Hook, one is before and the other is after, and the principle of its implementation is realized by the slot of art, which can add two slots before and after the originally called method, and then go to execute our hook, which can be understood figuratively as the following figure.

As we can see from the figure, the target App is mainly composed of two parts, the first is the MainActivity main class, and there are two methods in the class, one is the onCreate method, which is a method of MainActivity initialization, and the second is the getFlag method, this method is also our target, by Hooking this method, we can Through this method, we can know what the MD5 value representing the flag is.
Our idea is to Hook the getFlag method first. Assuming we Hook the getFlag method, we are naturally most concerned about the incoming string value, and the specific Xposed module code is as follows.

In this way we can get the MD5 value we want, and then modify the parameters to achieve control of the app.

How to fight Hook attacks?
As the saying goes, if there is a spear, there is a shield. In response to Hook's attack, a defense has also been derived.
Since Xposed will call a specific ClassLoader when Hooking, then it is possible to detect the Xposed framework by loading the ClassLoader again, for example as follows.

1、Use the system API getInstancesOfClassesMethod to get the ClassLoader, through this way can only get once CL, we can traverse the Classloader used within the App.
- After traversing all CLs, we can detect its Hook by its member cache (target Hook method cache).


This detection method relies on the VMDebug.getInstancesOfClassesMethod() function provided by Android system, which only exists on Android 9-11, limiting the application of the solution. Moreover, as a counter-detection method, this key function can also be hooked by Xposed, and you only need to control the return of this function to complete the counter-detection.
In addition to the ClassLoader way to fight against Xposed Hook, there are other kinds of more traditional countermeasures, but they all have corresponding countermeasures, and the top image product has a unique countermeasure, and additional anti-detection and countermeasure technology, which can more accurately identify Hook risks.
Of course, at a deeper level, we can also use Hook technology to bring traditional Web attack techniques to the mobile side, and conduct offensive and defensive exercises in the mobile side to complement the skill tree as a red team, as well as against Hook technology and attackers to safeguard their own App security.
Overall, the offensive and defensive confrontation is a protracted war, requiring the continued efforts of security vendors.
In terms of offensive and defensive confrontation, based on years of technical accumulation, Top Elephant has achieved comprehensive security protection for Android, iOS, H5 and applets, effectively defending against debugging, injection, multiple opening, memory Dump, emulator, secondary packaging and log leakage and other attack threats. The unique "honeypot" function protects 16 kinds of data and files of Android, provides 7 kinds of encryption forms, and takes the lead in supporting source code free reinforcement for iOS.



