
Risk control strategy is a collection composed of rules and models and used to achieve risk control goals. Models and rules complement each other, complement each other, and focus differently in different business stages. During the launch period of new business, the data amount is insufficient and the strategy is mainly rules. When the business is running for a period, the data has accumulated, the exclusive model can be built to realize the convergence of model and rules.
The rules included in the risk control strategy include device dimension rules, behavior data rules, scoring card rules, black and white list rules, social communication rules, local and single dimension rules; the model is the law of the process and the whole.
Simple risk control strategies need to be developed and written independently, which requires a lot of manpower. With more frequent and complex illegal attacks, risk control strategies also need to be quickly updated and updated.
The Dinsight real-time risk control engine provides a visual interface that allows business people to quickly get started and configure new risk control strategies. After entering the user name and password, click to log into the risk control decision engine. Users can customize policies according to business requirements and maintain policy information. Support management policies according to the directory, view the hierarchical relationship of products, events and policies, and quickly locate policies and policy nodes through the directory to view details.
query strategy. In the Policy Management list interface, the policy is displayed by Product and can be viewed through the dendrogram on the left side of the page; the default displays the policy under all products.

** New strategy**. On the Policy Management list interface, click the New Policy button to jump to the New Policy page.
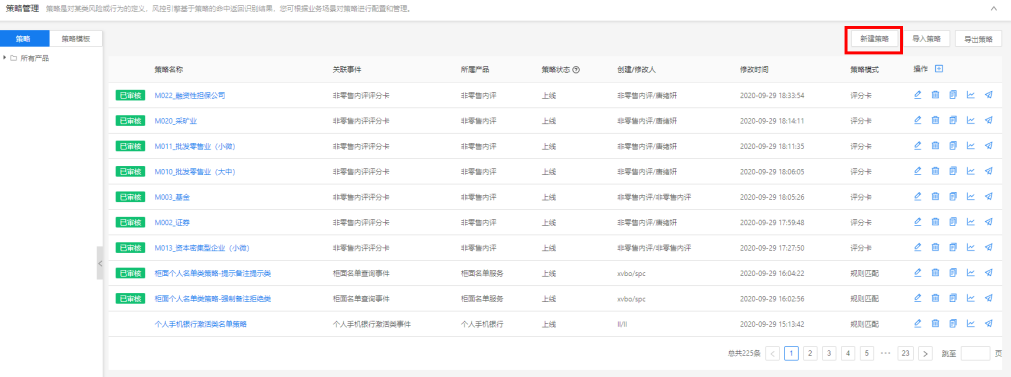

Multiple policies can be created under the same event, and the order of execution of the policy under the same event is determined by the priority. The smaller the number, the higher the priority, and 0 represents the highest priority. If the proportion of requests that pass through this policy is set 80%, 80 out of 100 requests pass through this policy, and another 20 requests skip this policy to execute other policies. Furthermore, the policy is executed when the conditions are met.
Edit policy. In the Policy Management list interface, on the right side of each policy data, click the edit "" button in the operation bar to jump to the policy edit page.




Deletion policy. In the Policy Management list, click the Delete "" button in the operation column to pop up a warning and give a prompt " Do you confirm to delete the component?”

Click the [Cancel] button, the index data does not change; click the [OK] button, the data to be deleted should be submitted for review. If the review passes, the deletion is successful; if the audit refuses, the deletion fails.
Replication strategy. In the "Policy Management" interface, in the right operation bar of each policy data, click the Copy "Copy" button, and the interface will jump to the "Copy" interface, which can copy this policy, and modify the configuration information to generate a new policy. After copying, the policy name should be re-entered, and other contents remain unchanged and can be modified.

Strategy trend chart. In the "Policy Management" interface, in the right operation bar of each policy data, click the trend chart button, the interface will jump to the "Policy Trend Display" interface, you can see "Hit Trend" and "Execution".

Dinsight can perform risk judgment on the requests sent by the business front end in marketing activities, payment orders, credit applications and other scenarios, and return the decision result within milliseconds to improve the risk prevention and control ability of the business system. The average processing speed of daily risk control strategies is less than 100 milliseconds, the aggregate data engine, the integration of expert strategies, the parallel monitoring, replacement and upgrading of existing risk control processes, and the construction of a dedicated risk control platform for new businesses; Aggregate anti-fraud and risk control data, support multi-party data configuration access and precipitation, can be configured graphically, and quickly applied to complex strategies and models; Based on the experience reserve of mature indicators, strategies and models, as well as deep learning technology, self-performance monitoring and self-iteration mechanism of risk control can be realized; Integrated expert strategy, based on system + data access + index library + strategy system + expert implementation of actual combat; It supports parallel monitoring, replacement and upgrading of existing risk control processes, and can also build a dedicated risk control platform for new businesses.